Characteristics of eGovernment Services Requiring 2FA
/This post was originally a report submission for "NUS - eGovernment 2013" done by Ivan, Nasri, Kenneth, Zi Wei, and myself.
Introduction
In order to determine if an eGovernment service needs to be protected by 2FA, the assurance level of the service must first be determined. Assurance level is defined as the agency’s confidence level requirement that the user is who he claims to be.
There are two guidelines available online to determine the assurance level of a service:
- Office of Management And Budget M-04-04: E-Authentication Guidance for Federal Agencies (United States, 16-Dec-2003)
- Department of Finance and Deregulation National e-Authentication Framework (NeAF) (Australian Jan-2009)
In M-04-04, 6 principles to determine assurance levels were defined, and NeAF has 10 principles. An initial look at both sets of principles shows that they are similar, and that the M-04-04 seems like a condensed collection of NeAF’s principles. Hence the report will use M-04-04’s 6 principles as a benchmark for analysis, as well as determine if a guideline set in 2003 is still relevant 10 years later.
M-04-04 defines four assurance levels, from Level 1: Little~no confidence, to Level 4: Very high confidence. This is derived from the potential impact of an authentication error, along with the likelihood of occurrence. There are a total of four levels of impact: None, Low, Moderate, and High. They, however, do not necessarily map directly to the assurance levels, but is derived from the matrix below:

For the purpose of 2FA, the report would go with a required assurance level of 3~4, requiring high confidence level of the user’s identity. We are assessing the service only against each principle, and not with the likelihood of compromise.
Principle 1 - Inconvenience, distress, or damage to standing or reputation
This principle talks about the potential of causing inconvenience, distress, embarrassment or damage to reputation with respect to a citizen’s government account being compromised.
Low impact (limited short-term inconvenience, distress or embarrassment to any party)
We examine the service to apply to speak at Speakers' Corner provided by NPARKS. Should the citizen’s account be compromised, this could allow the attacker to apply for such public speaking permit without the knowledge of the individual.
If the topic that is to be discussed is sensitive either to the country or to an individual, this could lead to a loss of reputation to the individual. However, the impact should likely to be short lived and limited, as this is a small-scale attack.
Moderate Impact (serious short term, limited long term inconvenience, distress and embarrassment)
We examine the example of rendered spent criminal record enquiry service provided by Singapore Police Force. This service allows the citizen to view the spent and current still active criminal records.
Should the account be compromised, the attacker could gain access to such information. Should the attacked be out to embarrass this individual, the attacker could diverge this information to the general public. This would cause tremendous damage and embarrassment to the individual and the effect could be long term should this person be a public figure.
More checks have to be conducted to ensure that the user is who he claims to be before allowing him/her to have access to this information. Using 2FA would provide higher assurance on this.
Serious Impact (serious long term damages of any party)
In the case of serious impact, which is large scale and long term, we look at the impact of an impression attack to the government. Taking the example of CPF portal, should an attacker succeed in viewing an individual CPF detail and even publish this, or boost online that he managed to hack in, this would cause a distrust by citizens on this service and ultimately, to the government.
This would cause long-term damage to the reputation of the government. Thus, government has to spend effort in ensuring the safety of individual data. 2FA would come in to ensure that the proper authorization is made before an individual could view these individually sensitive data.
Principle 2 - Financial loss or agency liability
This principle discuss about the potential of financial loss with respect to a citizen’s government account being compromised.
Low impact (insignificant or inconsequential unrecoverable financial loss to any party or agency liability)
Using the Ministry of Manpower (MOM) to calculate your salary and overtime pay is open to all users. There is no verification of documents for the salary as it is to provide a general online simple tool to guide workers in Singapore on the calculation. Results are short-lived and it does not retain the data.
Moderate impact (serious unrecoverable financial loss to any party, or a serious agency liability)
Baby Bonus Online Enquiry System by Ministry of Family and Social Development has an online enquiry service to allow you to view a citizen child's cash gift disbursement and Child Development Account (CDA). Such cash gift information is standard across every citizen’s child and the context is limited to a certain age group. Moreover, the usage of CDA is controlled and errors do not cost a significant impact to finances. 2FA would help to mitigate the risk of compromise for this service.
High impact (severe or catastrophic unrecoverable financial loss to any party; or severe or catastrophic agency liability)
If we take a look at the IRAS's myTax electronic service by Singapore government, there are severe impact should the information of taxation relating to either individuals or organization is inaccurate or obtained fraudulently. In the case of a large corporate such as IBM that does its business in Singapore, there will be loss of confidence if the staff that are not authorized to transact on behalf of it is able to make a transaction. Furthermore, there can be operational errors if a person with lower authority can easily make a transaction for a company. He may have submitted information that is incomplete from the organization tax submission point of view. All the above scenarios implies high risk and such events can result in a liability should the company shareholder's profits are impacted due to financial-related fines. In addition, there can be intangible loss of shareholder value in the company. Therefore, there should be 2FA for IRAS's myTax electronic service due to the risk profile.
Principle 3 - Harm to agency programs or public interests
This principle discuss about the potential impact of harm to agency programs or public interests. In below analysis, assets can include both physical and financial types.
Low impact (limited adverse effect on organizational operations or assets, or public interests)
NPARKS has an online website that allows citizens and non-citizens to book a barbeque pit in selected public parks. This public facility is low-cost and the consequences both physically and financially are not significant.
Moderate impact (serious adverse effect on organizational operations or assets, or public interests)
Firstly, a major service that can have an impact of finance is the HDB Housing Loan Lump Sum Payment with CPF. Although, housing purchases are not frequently transacted per individual, the financial bearing will affect for a long period of time. Therefore, it is important that transaction should have high assurance albeit not critical. 2FA is a possible implementation for this service.
High impact (severe or catastrophic adverse effect on organizational operations or assets, or public interests)
The other major service that if it is compromise and also link to the above IRAS's service in principle 2 or HDB Housing Loan Lump Sum Payment with CPF is the CPF account’s online services. In this service portal, there is much information that pertains to the individual, primarily the contribution to the central fund. Given the contribution, the income of the individual can be derived from using known contribution rates. For self-employed who declare their business income or personal income, inaccurate or false declaration of income will result impact to the subsidies, grants or allowances that the Singapore government provides. There is an impact to Singapore economic interest and such to investor’s confidence and trust in the system.
For CPF account’s online services, due to the interlink relationships of the various agencies interest and how the public is affected, 2FA should be implemented for this eService.
Principle 4 - Unauthorized release of sensitive information
This principle focuses on the potential impact and risk of unintentional and unauthorized releases of the confidential or sensitive data of a particular person, governments or commercially sensitive information to an unauthorized third party who does not possess the right to own or know such sensitive information. The principle categorizes the level of impact by the impact of loses of confidentiality.
Low impact (limited release of personal, government sensitive, or commercially sensitive information to unauthorized parties resulting in a loss of confidentiality)
With LTA Fines, the impact of the unauthorized releases of the confidential data is Low. This is due to the nature of the LTA Fines system, which stores and process only vehicle related information and the fines related information. Hence, exposure of the confidentiality to unauthorized parties does not give significant impact to the affected party.
Moderate impact (release of personal, government sensitive, or commercially sensitive information to unauthorized parties resulting in loss of confidentiality with a moderate impact)
With CPF Account, the impact of the unauthorized releases of the confidential data is Moderate. The CPF account information generally holds the contributions and transactions related to the only within the CPF account. Hence, releasing of such data may bring annoyance and inconvenience to the victims. However, there may not be leading to threats to one-self’s personal safety. Thus it would help to secure the eService with 2FA.
High impact (release of personal, government sensitive, or commercially sensitive information to unauthorized parties resulting in loss of confidentiality with a high impact)
With MyTax Portal, the impact of the unauthorized release of the confidential data is High. As the portal stores information about incomes of a particular person, together with some important investment information (e.g.: insurance, share profits, etc.), hence releasing of such information to a third party may resulted in unwanted harassments or lead to safety threats if unauthorized party who possess this information demands monetary return from the victims. It would be critical to protect MyTax Portal with 2FA.
Principle 5 - Personal safety
Among all electronic government services that requires electronic authentication, two main categories of electronic services can potentially affect personal safety if the electronic authentication is not properly and correctly implemented. The two main categories are those electronic services that deal with health or medical systems and those that deal with public safety and emergency response systems.
Low impact (minor injury not requiring medical treatment)
Health Sciences Authority – Listing of approved medical and cosmetic products. Should these electronic services be compromised and information altered, the list of approved medicines and medical products can potentially contains those products that are found to be harmful to the human and is banned in Singapore. This incorrect information can result in Singaporeans using harmful medical or cosmetic products that can cause various side effects like diarrhoea and damage to the skin. Access to the system that store the list of approved products should therefore be 2FA enabled so that we can be assured only authenticated authorised personnel can update and alter the information.
Moderate impact (moderate risk of minor injury or limited risk of injury requiring medical treatment)
Singapore General Hospital – Medical report request form. Should the hospital health care system containing patients’ medical history, drug allergies and medication records be compromised and altered, medical report generated can contain the wrong medical information thus resulting in incorrect administration of medical treatment and drugs to patients subsequently. This error may have adverse effect on the well-being and personal safety of the patient if the patient has allergies to the drug that is incorrectly administered. In the worst case scenarios, death or permanent disabilities may happen to the patients. Thus, it is critical that this eService be 2FA enabled.
High impact (risk of serious injury or death)
Singapore General Hospital – Visitor Management System for Contact Tracing and Singapore Police Force – Report a Crime. The above two electronic services are some form of public safety and emergency response system where timely response to the right location with the right resources and information is critical to save lives in times of an emergency situation like an accident, disaster or terrorist attack. For example in time of SARS or H1N1 outbreak, the accuracy and integrity of the information captured in the Visitor Management System for Contact Tracing can assist the Authority to quickly identify and track down all the people that are in contact with certain affected patients so that they can be quickly quarantine to prevent the further outbreak and wide spreading of the air-borne diseases, thereby saving even more lives. Thus, it is critical that this eService be 2FA enabled.
Principle 6 - Civil or criminal violations
This principle assesses the criminal impact if a service performs an operation on behalf of a compromised identity.
Low impact (risk of civil or criminal violations of a nature that would not ordinarily be subject to enforcement efforts)
This level of impact would potentially cover all scenarios where a user had impersonated as another user when using an eService, without the other user’s permission. Such an unauthorized action would constitute civil/criminal violation, but if no damage is performed, might not be ordinarily subject to enforcement efforts. It is still a crime, nevertheless.
Moderate Impact (risk of civil or criminal violations that may be subject to enforcement efforts)
The Singapore Police Force offers the Electronic Police Centre service, where citizens can make a police report online using SingPass. Under the Singapore Law, making a false report would be a criminal offense, so it is imperative that the service is absolutely certain of the reporter's identity, to deter false reports.
At this stage of assessment of simply the impact, this service should warrant 2FA to increase the assurance level of the user.
High Impact (risk of civil or criminal violations that are of special importance to enforcement programs)
The M-04-04 cited an example of unauthorized access to a law enforcement database containing criminal records could compromise investigations as high impact. However, a review of existing public eServices does not reveal any service that matches this level of impact.
It would appear that the ministries are hesitating to provide such sensitive G2C (or even G2B) services. To find services that could match this, G2G services should be evaluated instead, e.g. a mechanism to share info to cooperate on combating organized crime & illegal trafficking activities (e.g., UN Convention Against Transnational Organized Crime).
Summary & Recommendations
As it stands, all the principles are very useful in assessing eService for their assurance level, and still relevant in today’s context. In many cases, a single service could easily fall into the moderate/high impact grading of multiple services (for example, Singapore Police Centre – Report a crime is High Impact for Personal Safety and Moderate Impact for Civil or criminal violations, and MyTax Portal is High Impact for both Financial loss or agency liability and Unauthorized release of sensitive information). Evaluation of a service should be performed on all the principles for a complete overview of a service’s risk outlook, and the final assurance level should be given base on the principle with the highest impact.
However, prior to assessing the service against the impact, the government should perform the following activities beforehand:
- Agree on the definitions of short, mid, long term duration (if relevant to the service)
- Agree on the definitions of limited, moderate serious impact (if relevant to the service)
- Agree on how to quantify certain risks, e.g. personal safety. This is especially critical in an environment where most assessments are monetary cost-benefits analysis. In such an environment, the government likely could only assess a service well base on Principle 2 – Financial loss or agency liability. For services meeting other principles, they would be skewed towards low assurance requirement.
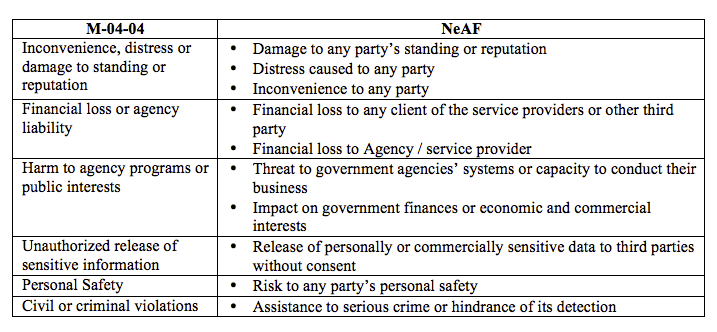
In comparison with the NeAF principles, we are able to find mappings from M-04-04’s to NeAF’s (refer to Appendix A: M-04-04 to NeAF Mapping). If we are to apply the same set of principles to a service, it is highly likely that the service will receive the same treatment in terms of decision to implement 2FA. However, there are a few cases where NeAF’s framing of the risks are clearer, without detailed explanation of the impact, whereas the M-04-04’s version required some detailed thought of the possible impact. A simple example would be “Principle 3 Harm to agency programs or public interests”, where NeAF had framed it as “Threat to government agencies’ systems or capacity to conduct their business”, which further describes it as capacity to conduct their business. Similarly, for “Principle 6 Civil or criminal violations”, where NeAF framed it as “Assistance to serious crime or hindrance of its detection”. Most would had considered the aspect of assistance to serious crime, and few would consider the aspect of hindrance of its detection. Moving forward, for better understanding and clarity, it would be better for government agencies to adopt the NeAF’s framing instead. The simple framing of words could help evaluators look at the service in different light.
However, applying the principles by themselves is not sufficient. As suggested by M-04-04 and NeAF, the likelihood of compromise should be considered along with the impact to derive the final assurance level.
On top of the likelihood factor, the following factors should be considered as well as part of the entire 2FA consideration process, although they are not part of the principles:
- User Experience: User experience would suffer due to the extra steps required to perform the 2FA. This might deter the user from using the service frequently, or ever again in the future. This factor is especially applicable to the Electronic Police Centre eService. Although the service warrants 2FA, such an implementation might deter users from lodging genuine criminal case, or further drive them to the manual process of phone calls/walk-in to police station, which defeats the original intention of the eService. Such deterrence must be justified in regards to the risk of compromise.
- Capital Cost: This will be directly related to the selected 2FA solution and the user size. A cost-benefit analysis must be performed for the various available 2FA solutions, such that the cost of implementation will out-weigh with the risk impact. This is especially crucial for services with assurance level 3, which is high enough to consider for 2FA, yet not critical enough to mandate 2FA.
- Operating Cost: Most implementation of 2FA would require the user to have a higher level of IT literacy when using the service. If the literacy level is not high, more training / education would be required in order to allow its citizen to use the e-government services. Support desk would also be required, and all these translate to higher training and support cost. In addition, some 2FA solutions charges for each transaction (or every 1000 transactions). This translates to an increase in operating cost. The operating cost must justify the risk of compromise.
Appendix A: M-04-04 to NeAF Mapping